On August 20, 2021, China's legislature, the Standing Committee of the National People's Congress, finally passed the Personal Information Protection Law (the "PIPL") after three rounds of review. Effective on November 1, 2021, the PIPL, together with the Cybersecurity Law (the "CSL", effective on June 1, 2017) and the Data Security Law (the "DSL", effective on September 1, 2021), further completes China's legal infrastructure in the field of cyber security.
Here we are going to take a fresh glimpse into the PIPL's rationale and key rules, and then, to provide some preliminary thoughts and tips for compliance.
RATIONALE OF THE PIPL
1. Multi-layer Approach to Personal Information Protection
The PIPL adopts a differentiated protection strategy based on the types of personal information and processing activities. For general personal information and routine processing activities, the PIPL requires sufficient notification and explicit consent, or other lawful basis. For sensitive personal information and high-risk processing of data, processors are required to meet special requirements in addition to general obligations. For instance, processing of sensitive personal information must be based upon specific objectives with sufficient necessity, and such necessity and influence on personal rights and interest should be notified to the individuals involved. In cases where consent is the base for legitimacy, such consent should be in the forms of separate consent or written consent, and assessment of influence on personal information protection should be conducted prior to processing. Personal information of minors aging under 14 should be uniformly regarded as sensitive personal information and any processing of such information should be based on consent from the minors' guardians. Stricter requirements of compliance come in for certain activities, including the automatic decision-making process based on personal information and the installation of image collection or personal identification equipment.
2. Uniform Application to Online and Offline Activities
Unlike the personal information protection rules under the CSL which only apply to cyberspace, the PIPL does not close doors for the protection of non-electronic personal information, nor does it distinguish between online and offline personal information processing activities. In short, the PIPL provides a unified protection mechanism for various forms of online and offline personal information. Activities of processing personal information by traditional means (such as by paper or manually), and by means of combining online and offline (e.g. O2O), are both subject to the PIPL.
3. Shift towards Diversified Lawful Bases
Both the Decision on Strengthening Protection of Network Information promulgated by the Standing Committee of the National People's Congress and the CSL provide that individual consent is the only lawful basis for processing personal information. However, it is neither necessary nor practical to solely rely on individual consent as the lawful basis for processing personal information, and it is also inconsistent with relevant foreign practice. In order to ease the rigidity of relevant provisions under the CSL, Articles 5.6 and 9.5 of the Information Security Technology-Personal Information Security Specification (the "Personal Information Security Specification") set up exemption rules in terms of individual consent. Although the Personal Information Security Specification meets the needs in practice to some extent, as a recommended national standards at a low level, it is not able to provide a solid legal basis for lawful processing of personal information. It is exactly the case for lawsuits where the Personal Information Security Specification cannot be used as an effective defense.
Against this background, Article 13 of the PIPL, by reference to foreign legislations, expands the lawful bases of processing personal information containing:
- where consent is obtained from the individual;
- where it is necessary for entering into or performing a contract to which an individual is a party, or for implementing human resources management pursuant to employment policies legally established and collective contracts legally concluded;
- where it is necessary for fulfilling statutory duties or obligations;
- where it is necessary for responding to public health emergencies or protecting life, health and property safety of a natural person in case of emergency;
- where the personal information has been made public either by the individual or by other lawful means and the processing of such information is limited to a reasonable scope in accordance with this Law; and
- other circumstances stipulated by laws and administrative regulations.
Under the EU's General Data Protection Regulation (the "GDPR"), the most flexible lawful basis is that processing is necessary for the purposes of the legitimate interests pursued by the controller or by a third party unless legitimate interests are overridden by the interests or fundamental rights and freedoms of the data subject. The PIPL has not explicitly introduce such mechanism, but the term "where it is necessary for implementing human resources management pursuant to employment policies legally established and collective contracts legally concluded" is added to the lawful basis of "necessary for entering into or performing a contract" under item b, which could be considered as introduction of the "legitimate interests" clauses in the field of labor and human resources. In addition, the catch-all provision of "other circumstances stipulated by laws and administrative regulations" under Item (f) also leaves room for further expanding lawful bases based on future practice.
The diversification of lawful bases is one of the major changes brought about by the PIPL, which provides more flexibility for collecting, using and sharing data for enterprises, and is expected to have a positive impact on relevant industries. However, it also raises new issues, namely, how to accurately define, properly choose and reasonably construct lawful bases in practice, and how to avoid the lawful bases being held invalid.
4. Coverage of the public sector
On the basis of stipulating the rules of processing personal information that all types of processors must generally abide by, the PIPL also sets forth special provisions for processing of personal information by state organs. While satisfying the needs of state organs to perform their duties, their processing of personal information is appropriately restricted, so that state organs could not excessively use technical means and state machinery to interfere with private lives.
Article 37 of the PIPL stipulates that the provisions of this Law relating to the processing of personal information by state organs shall apply to the processing of personal information by any organization with public affairs management function authorized by law or regulations.
5. Comprehensive internal and external protection
When the global scramble for data sovereignty is heating up, the PIPL, based on the DSL, also pays attention to strengthening the cross-border data supervision by setting forth a special chapter on the cross-border provision of personal information.
Article 36 of the PIPL requires that domestic processors take necessary measures to ensure that the processing of personal information by overseas recipients meet the PRC's personal information protection standards. This requirement is basically consistent with GDPR's principles and objectives for cross-border supervision of personal data. However, different from GDPR, the PIPL, based on the actual situations of the PRC, does not introduce the "whitelist" system of European Union.
On the basis of Articles 25 and 26 of the DSL, Articles 42 and 43 of the PIPL further stipulate the control system on exporting personal information and extraterritorial reciprocal protection mechanism, clarifying that China's National Cyberspace Administration may put overseas entities that endanger the national security, social public interests and personal information rights into the list to which provision of personal information is restricted or prohibited, and may take countermeasures in response to countries that take discriminatory prohibitions, restrictions or other similar measures against the PRC in respect of personal information protection.
KEY RULES OF THE PIPL
1. Rules on Notification and Consent
The PIPL reconstructs the notification and consent rules to a large extent with nearly one third of the whole text, which is also one of the major changes brought about by the PIPL.
Article 18 clarifies the basic content and effective form of notification, and Article 14 clarifies the basic meaning of legitimate and valid consent. These two provisions basically follow the practical rules established by the Personal Information Security Specification. On this basis, Article 18 adds exemption from notification, namely, it is allowed not to inform the individual if such matter shall be kept confidential or is not required to be disclosed according to laws and administrative regulations provide that information shall be kept confidential or it is not necessary to notify the relevant individuals; however, if, for the protection of life, health or property safety of a natural personal in the event of emergency, the individual shall be informed in a timely manner after the emergency is cleared. We believe that notification and consent are the two obligations of processors corresponding to the individuals' rights to know and make decisions respectively. The relationship between these two is that notification is a prerequisite for consent, the right to know is prior to the right to make decisions, and in the absence of notification there can be no consent but not vice versa. As a result, the circumstances under which notification is exempted are fewer than those where consent is not required (i.e. by application of other lawful bases). If notification is exempted, the individual's consent is not required naturally; however, if consent is not required, the right to be informed will not be certainly released unless it is under the particular circumstance under which notification is exempted.
Article 14 of the PIPL stipulates that the forms of consent include voluntary and express consent, separate consent and written consent. Voluntary and express consent is a general requirement for consent, while separate consent and written consent are special requirements. The application circumstances are as follows:
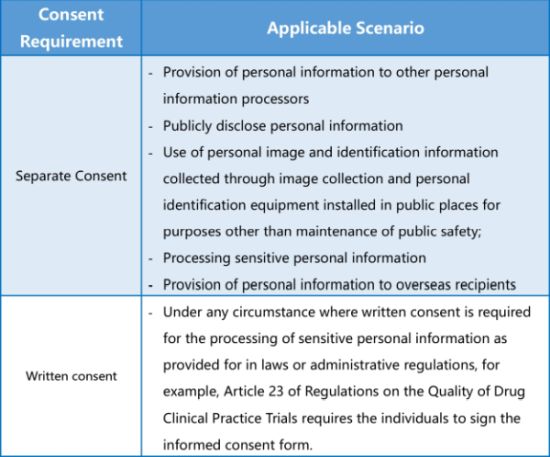
The PIPL does not specify what "separate consent" means. In literal terms, separate consent should be distinguished from package consent that binds multiple business functions or types of information, and the express standard shall be met.
The PIPL neither specify what "written consent" means. In accordance with Article 469 of the Civil Code, in addition to the forms by which any content carried can be represented in a tangible manner, such as a written contract, letter, telegram or telex, etc., "written form" also include data messages that can tangibly represent the contents contained by means of electronic data exchange, e-mail, etc., and can be accessed for reference at any time. According to this definition, when a user clicks and checks the box of "Agree" on the website or APP page, such forms of network operation records will be stored in the server in the form of data and can be accessed for reference at any time thereafter. It seems to meet the requirement of written form. However, there is no different from consent in general form. The significance of emphasizing written consent in the PIPL warrants further discussion. In addition, it needs to be further clarified whether written consent also includes consent given by an individual in telephone recordings or videos.
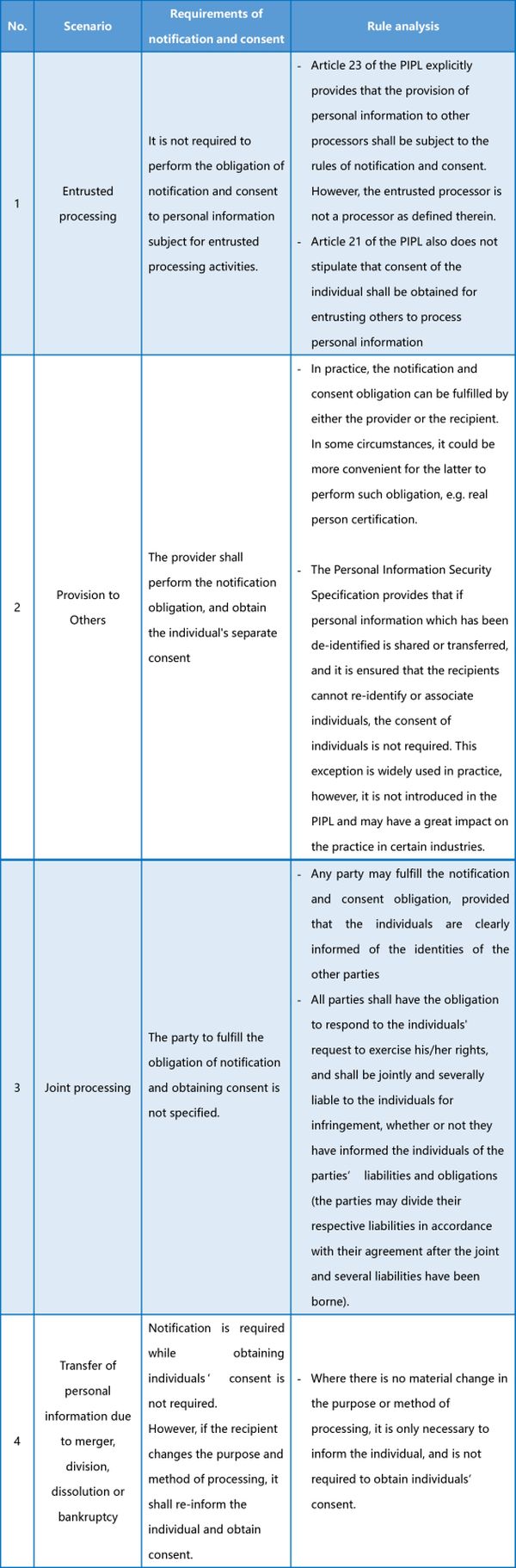
Under the PIPL, the rules of notification and consent under special circumstances are as follows:
2. Rules on Installation of Image Collection and Personal Identification Equipment in Public Places
Article 26 of the PIPL provides that, the installation of image collection equipment and personal identification equipment in public places shall satisfy all the following requirements:
- Restriction on purpose: necessary for maintaining public security;
- Additional requirement on notification: prominent signs shall be set up;
- Restriction on using personal information for other purposes: shall obtain individuals' separate consent.
Image collection equipment and personal identification equipment as provided herein are not limited to facial recognition equipment, because image collection equipment and personal identification equipment do not necessarily use facial recognition technology. For example, security surveillance video can collect personal images, but do not use facial recognition technology for analysis, verification and identification; and personal identification equipment may use either facial recognition technology, gait recognition or voice recognition technology. Therefore, the scope of application of Article 26 is apparently broader than Provisions of the Supreme People's Court on Several Issues concerning the Application of Law in Hearing Civil Cases with Respect to Using Facial Recognition Technology to Process Personal Information (the "Judicial Interpretation on Facial Recognition").
Article 26 is applicable only in public places. As to what public places means, the PIPL does not provide clear interpretation. Referencing to Article 2 of Regulations on Sanitation Management of Public Places and general rules of thumb, places that are accessible to unspecified individuals, including hotels, restaurants, barbershops, beauty salons, cinemas, theaters, parks, shopping malls, bookstores, waiting rooms in hospitals, waiting rooms for bus stations (airports and piers), and public transportation vehicles, should all be regarded as public places. Item 1 of Article 2 of the Judicial Interpretation on Facial Recognition and Appendix D of the Guidelines on Notification and Consent for Personal Information (Draft for Comments) provide similar definitions of public places. However, both terminology of "business premises" and "public places" are used in the Judicial Interpretation on Facial Recognition. It remains to be seen whether there is any difference between the two.
With regard to the restriction on purpose, there are three possibilities: there is no purpose to maintain public security, only for the purpose of maintaining public security, and both to maintain public security and other purposes. However, in the first scenario, the purpose restriction is not satisfied even if individuals' consent is obtained; while in the latter two scenarios, the purpose restriction is satisfied.
In terms of the meaning of "public security", referencing to the elements of the crimes of endangering public security, public security refers to the life and health of unspecified majority of people, the safety of major public and private property and the safety of public production and living, the core of which lies in the non-specificity of the protected object.
As for setting up prominent reminding signs, ensuring that individuals have a "general threat perception" of the information collected by the devices shall be taken as the standards. That is, the area covered by the device can be known by the public, and such device cannot be installed in a secret place unknown to the public. It emphasizes that ordinary reasonable people can perceive the threat of invasion of privacy and will not have any reasonable expectation of privacy. In addition, setting up prominent reminding signs is only an additional notification requirement, which cannot replace the notification and obtaining consent processing by the processors, which still need to abide by the general rules of notification and consent.1
Under the multi-layer restrictions set by Article 26, the use of facial recognition technology for precise marketing and other applications in smart retail scenarios will face severe compliance challenges.
3. Rules for Using Personal Information in Automated Decision-Making
Based on the reference to GDPR and domestic practice, Article 24 of the PIPL puts forward the basic regulatory requirements for automated decision making and personalized display, which preliminarily responds to the social concern about "big data killing". It is a limited exploration of algorithm supervision. However, algorithm supervision is a systematic and cutting-edge project. The current laws only sporadically involve this issue, and it needs more research, exploration and overall design.
Article 24 provides for both automated decision-making and personalized display. The two are related, but are two types of activities.
According to Article 73, automated decision-making refers to the activity of automatically conducting any analysis or assessment of the behavior and habits, interests and hobbies, financial, health or credit status or other information of an individual, and make decisions through a computer program. Further referring to Article 22 of the GDPR and the Guidelines on Automated individual decision-making and Profiling for the purposes of Regulation 2016/679 published by the WP29 Working Group, automated decision-making may rely either on the data of user profiling or other data. No matter what kind of data the automated decision-making is based on, the bottom line is that, it is based on technology to help personal information processors to make decisions, and such decisions may have a significant impact on the individuals' rights and interests of the personal information subject, especially negative impact, for example, the decision made based on automated decision-making is to refuse to grant loans to a borrower. Therefore, the processor should ensure the transparency of its decision making and the fairness and impartiality of its results, and should not make unreasonably differentiated treatments to individuals with respect to transaction conditions such as price. When the processor makes decisions that have significant impact on individuals' rights and interests, the individuals have the right to request explanations from the processor, and also the right to reject the decision made by the processor only through automated decision-making.
With regard to personalized display, by reference to Article 3.16 of the Personal Information Security Specification, "personalized display" means activity of displaying information or providing search results for products or services to personal information subjects based on their personal information, including their web browsing history, interests, consumption records and habits The purpose of personalized display is to influence the choice and decision of the individual, not the decision of the processor itself. As for this, Article 24 (2) of the PIPL requires that individuals be given autonomous control, which is, processors should provide options not tailored to personal characteristics or provide convenient means of rejection to individuals.
4. Rules for Cross-border Transfer of Personal Information
Article 38 of the PIPL expands the scope of entities subject to rules regulating cross-border transfer of personal information from critical information infrastructure operations ("CIIO") as stipulated by the CSL to all personal information processors.
According to Article 39, cross-border provision of personal information must satisfy the following preconditions:
- Personal information subjects shall be informed of the situation of cross-border provision of personal information, such as the recipient of personal information, the type recipient of personal information, the types of personal information provided, etc. However, if it is within the scope of exemption from notification, the party is not required to fulfill its duty of notification;
- If consent is used as the lawful basis of processing personal information, separate consent of the individual is required. If other lawful basis is relied on, no consent is required;
- The overseas recipient is not included by the national cyberspace administration authority in the list of entities which provision of personal information is restricted or prohibited.
Subject to the satisfaction of the preconditions, cross-border provision of personal information also requires to follow the appropriate legal path in accordance with Article 38:
- For CIIO and personal information processors whose processing of personal information reaches the threshold amount prescribed by the national cyberspace administration authority: On the basis of local storage, if it is indeed necessary to provide personal information to overseas recipients, security assessment organized by the cyberspace administration authority shall be conducted, unless otherwise prescribed;
- Other personal information processors: they may choose one from the following three ways, pass the certification process of personal information protection of professional agencies, enter into the standard contract formulated by the cyberspace administration with the overseas recipient, or follow other statutory paths.
5. Rights of personal information subjects
According to Articles 44 to 47 of the PIPL, personal information subjects enjoy many rights, which can be roughly divided into the following two parts:
- Basic rights: the rights to be informed, to make decisions, to restrict and refuse personal information processing activities. The right to be informed is the premise and basis for the right to make decision and other rights; the right to restrict and reject processing is the dissemination of the decision-making right.
- Specific rights: right of access, right to obtain copies, right of rectification, right of deletion and right of portability of personal information.
Compared with existing rules, the PIPL adds the portability right and arrangements for the relatives of the deceased to exercise the personal information rights of the deceased.
Whether to introduce the portability right was controversial during the legislating process of the PIPL. Article 45 stipulates that if an individual requests to transfer his personal information to a personal information processor designated by him, which meets the conditions prescribed by the national cyberspace administration authority, the processor requested shall provide a channel for transfer. While introducing the portability right, it adds the restriction of "meet[ing] the conditions prescribed by the national cyberspace administration authority", which provides flexibility. If there are difficulties in technical realization and cost tolerance at present, the cyberspace administration authority may limit the scope of application and impose more conditions, which will be gradually relaxed in the future.
As for the personal information of the deceased, Article 49 stipulates that, upon the death of a natural person, his/her close relatives may, for their own legitimate and rightful interests, exercise the rights to access, obtain copies, rectification and delete of the relevant personal information of the deceased, unless otherwise arranged by the deceased during his/her lifetime. Compared with the Draft of the PIPL, this arrangement better balances the interests of the deceased and his/her close relatives. However, Article 994 of the Civil Code stipulates that the personality rights and interests of the deceased, such as privacy, are still protected by law. If the close relatives of the deceased exercise the rights to the personal information of the deceased for their own interests, they may conflict with the personality interests of the deceased, the interests or will of other close relatives. How to coordinate the conflicts among the three remains to be tested in judicial practice.
6. Special Obligations of the "Gatekeeper"
Article 58 of the PIPL adds "gatekeepers' obligations" for large internet platforms to protect personal information, requiring personal information processors which are providers of important internet platform services, have a large user base and operate a complex business type to fulfill the following obligations:
- Establish a sound personal information protection compliance system in accordance with state regulations, and establish an independent body mainly composed of external members to supervise personal information protection;
- Follow the principles of openness, fairness and impartiality, formulate platform rules and clarify the obligations of product or service providers within the platform to regulate processing of personal information and to protect personal information;
- Cease to provide services for products or service providers on the platform which process personal information in serious violation of laws and administrative regulations;
- Release reports on social responsibility of personal information protection on a regular basis, and accept public supervision.
These "gatekeepers" are key to personal information processing in internet ecosystem. They offer the providers of products or services on their platforms (such as App, mini program, public account and SDK, hereinafter referred to as the "service providers within the platforms") with access services (including distribution, downloading, update, etc.), operations, technical resources and information collection channels, as well as market and users access channels. Large internet platforms could be the first line of defense to manage and control personal information compliance of the service providers within the platforms based on its technology and operation environment restrictions imposed on the service providers within the platforms.2
However, the PIPL does not clearly define the standards for determining "important internet platforms", "have a large user base" and "operate a complex business type". In reference to the Interim Provisions on the Administration of Personal Information Protection of Mobile Internet Applications (Draft for Consultation), Daodou v. Baizan and WeChat Case and Professor Zhang Xinbao's opinion, the following types of internet platforms will be identified as "gatekeepers":
- Mobile application distribution platforms;
- Intelligent terminal operating system service providers; and
- Internet platforms that provide basic network services, such as platform-based APPs providing automatic network access or automatic transmission service, such as WeChat with mini programs.3
7. Penalties and Remedies for Violations
Chapter 7 of the PIPL properly links up with civil law, administrative law and criminal law, and clarifies the legal liabilities for violation of personal information protection obligations. The highlights include:
- The administrative penalty stipulated by Article 66 of the PIPL has a considerable deterrence effect. According to this Article, the violator which commits illegal processing of personal information or fails to fulfill the obligation of protecting personal information could be imposed a fine up to 50 million yuan or up to 5% of last year's annual revenue. The objects subject to such penalties include both the processors and the agents entrusted to process personal information
- Article 69 of the PIPL establishes the rule of constructive fault, that is, if the processor cannot prove that it is not at fault when it infringes personal information rights and interests, it should bear tort liability such as paying damages. This Article also clarifies the compensation criteria for infringement of personal information rights and interests. If the personal information rights and interests are infringed due to the processing of personal information, the liability for damages shall be borne by the processor determined based on the loss incurred to the infringed individual, or the gains derived from the infringement by the processor. If the loss or benefits are difficult to be ascertained, the People's Court may determine the amount of compensation according to the actual situation
- Article 70 of the PIPL also provides for public interest litigation. A people's procuratorate, a consumer organization as specified by law, or an organization as determined by the national cyberspace authority may file a lawsuit with a people's court in accordance with law against a personal information processor whose processing of personal information violates this Law and infringes the rights and interests of a large number of individuals. Before the promulgation of the PIPL, Article 55 of the Civil Procedure Law and Articles 1 and 2 of the Interpretation of the Supreme People's Court on Several Issues concerning the Application of Law in the Trial of Civil Public Interest Litigation concerning Consumer Rights and Interests have provided legal support for public interest litigations against infringement of personal information. It is publicly reported that prosecutors in 14 provinces and municipalities, including Guangdong, Jiangsu, Zhejiang and Shanghai, have successively explored the possibility of including personal information protection into the scope of public interest litigation. Some prosecutors in Shenzhen, Fujian and Sichuan have filed public interest litigations collateral to criminal proceedings.
The above provisions of the PIPL will reverse the situation of weak protection of personal information caused by the high cost of rights protection, the difficulty of proving causation, and the low amount of damages.
TIPS FOR COMPLIANCE FOR BUSINESS ENTITIES
The PIPL provides diversified legal bases for processing personal information and thus provides enterprises with more flexibility to lawfully process personal information. Enterprises may adjust to use other lawful basis, according to the actual situation and upon comprehensive legal reasoning, where it is unable to difficult to obtain individuals' consent at present. Businesses may even build a lawful basis within the scope of law based on the characteristics of the business.
The PIPL reconstructs the rules of notification and consent to a large extent, especially for sensitive personal information and high-risk processing activities, and puts forward the requirement of separate consent. How to understand "separate consent", how to harmonize "separate consent" for specific types of data or specific processing activities with the current practice of notification and consent based on business functions, how to achieve "separate consent" through product design, and whether it can be recognized by competent authorities and judicial authorities are major challenges faced by many enterprises, which need to be adjusted after comprehensive consideration upon product features.
The PIPL does not introduce the rule that "sharing of de-identified information does not require individuals' consent", which challenges the legality of data circulation businesses that previously relied on this rule. In this regard, enterprises can choose other lawful bases, or add user consent, or adjust the business model according to the actual situation of business.
The PIPL establishes a comprehensive mechanism for managing cross-border transfer of personal information, and the previously pending management system on the cross-border transfer of personal information for non-CIIO enterprises becomes a legal requirement. Businesses shall sort out the matters relating to the cross-border transfer of data, inform individuals of the information to be transmitted abroad by amending privacy notices or by other means, and obtain their consent unless other lawful bases can be relied on. On top of this, the enterprise shall enter into a standard contract (currently formulated by the national cyberspace administration authority) with the overseas recipient, and take necessary measures (such as contractual constraints, technical restrictions, regular reviews, compliance audits) to ensure that the recipient properly protects the personal information. After the state issues rules on certification of personal information protection in the future, personal information may also be transmitted abroad by means of certification.
Enterprises shall establish and improve response and process mechanisms for individuals' requests to exercise their rights, set up convenient channels for them exercising their rights, and timely respond to the requests of personal information subjects and the close relatives of the deceased to exercise rights. The portability rights newly added by the PIPL may be tried out with clear rules to the extent that is technically feasible and affordable; if there is difficulty in implementation, they may be put into practice after the competent authorities clarify the applicable conditions.
If overseas enterprises process personal information for providing domestic natural persons with products or services, or process personal information for the purpose of analyzing or evaluating the behaviors of domestic natural persons, regardless of whether they have any entities in the PRC, they shall set up a special agency or designate a representative in the PRC to be responsible for relevant matters of personal information protection, and report the name of the agency or the representative and the contact information to the competent authorities. This puts forward new requirements for overseas enterprises engaging in business operations in China. If such overseas enterprises have any entities in the PRC, they may designate the domestic entity to handle matters of personal information protection on their behalf; if such overseas enterprises have no entities in the PRC, they may appoint a lawyer or other service providers to handle matters of personal information protection on their behalf.
The PIPL requires enterprises not only to perform various personal information protection obligations, but also to establish a comprehensive internal governance system, including arrangements of responsible personnel for personal information protection, internal management system and operational procedures, technical measures of security, personnel management, emergency response and management, compliance audit, impact assessment, etc. These are relatively high requirements for small and medium enterprises. Only by taking these measures, can enterprises build a "bulwark", and establish a "safe harbor" to prevent risks.
Footnotes
1. Zhang Xinping, "Embedded Governance of Law and Technology in Intelligent Video Surveillance", in Legal and Social Development, No. 5, 2020.
2. Zhang Xinbao, Research on Setting Special Obligations for "Gatekeepers" of Internet Ecology to Protect the Personal Information of Personal Information, Volume 3, 2021.
3. Hangzhou Daodou Network Technology Co., Ltd., Changsha Baizan Network Technology Co., Ltd. and Shenzhen Tencent Computer System Co., Ltd. over the infringement upon the right to network dissemination of works and information, Civil Judgment (2018) Zhe 0192 Min Chu No.7184) of the Hangzhou Internet Court; Zhang Xinbao, Research on Setting Special Obligations for Internet Ecological "Gatekeeper" Personal Information Protection, Comparative Law Research, Issue 3, 2021.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.



