On July 7, 2022, 8 months since the release of a draft for public consultation, the Cyberspace Administration of China ("CAC"), China's cyber watchdog, released the final version of Measures for the Security Assessment of Outbound Data Transfer (the "Assessment Measures"), which are set to come into effect on September 1, 2022. An official Q&A regarding these Assessment Measures was also released by CAC on the same day.
The release of these Assessment Measures marks the finalization of China's security assessment rules of cross-border data transfer after the Cybersecurity Law of the PRC (the "CSL") first set out the security assessment requirements for transferring data outside of mainland. After the CSL, the Data Security Law of the PRC (the "DSL") and the Personal Information Protection Law of the PRC (the "PIPL") also require a prior security assessment before transferring overseas important data and personal information under certain circumstances, respectively. Therefore, the Assessment Measures provide detailed rules for implementing the relevant requirements of the CSL, the DSL and the PIPL.
According to Section 2 of the Assessment Measures, these measures apply to the security assessment for providing overseas the important data or personal information that is collected and generated by data handlers during their operations within the territory of the mainland. Under the DSL, a "data handler" is an entity or individual who carries out data processing activities, thus it could be one that determines the purposes and means of data processing (similar to "data controllers" under GDPR) or one that is entrusted by others to carry out processing activities (similar to "data processors" under GDPR).
Retroactivity of the Assessment Measures
It should be noted that although the Assessment Measures will come into effect on September 1, 2022 (the "Effective Date"), Article 20 stipulates its retroactive application: for cross-border data transfers that have been carried out before the Effective Date, if such transfers do not comply with the Assessment Measures, the rectification should be completed within 6 months upon the Effective Date, notwithstanding there is no further guidance on how to implement the rectification.
"Outbound data transfer" to cover remote access
Although the Assessment Measures do not define what would constitute "outbound data transfer", the official Q&A clarified CAC's official position on this issue. It clearly states that the "outbound data transfer" mainly includes two scenarios: (i) the data handler transfers or stores overseas data collected and generated in its operation within mainland; and (ii) the data collected and generated by the data handler is stored within mainland but can be accessed to or used by institutions, organizations, or individuals outside mainland.
This is the first time that CAC confirms that remote access to data stored within mainland by overseas entities or individuals would also constitute "outbound data transfer", thus would be subject to the same regulatory requirements for providing data to overseas recipients. With finger pointing surrounding the alleged remote access to U.S. user data by Chinese tech companies hitting headlines of international medias, this clarification makes no surprise and resolves the uncertainty that has been caused by the ambiguity of the provisions under the CSL and other laws.
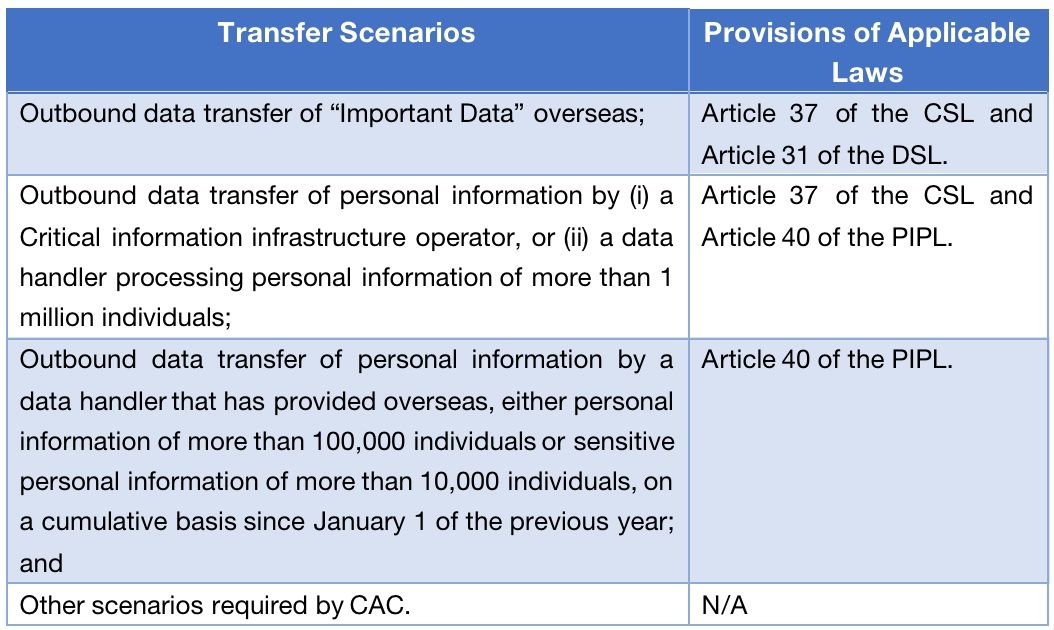
Four scenarios requiring filing for security assessment with the authorities
Section 4 of the Assessment Measures provides that under four scenarios, a data handler needs to file with the CAC through local cyberspace administrations at the provincial level, for security assessment of cross-border data transfer. The following chart describes those scenarios and the corresponding legal basis provided by provisions of applicable laws.
Prior risk self-assessment
In the draft version of the Assessment Measures published last October, a prior risk self-assessment was required for all cross-border data transfers. In Section 5 of the final version, the applicable scope of such prior self-assessment has been narrowed: prior self-assessment is only intended as a pre-step before the filing for security assessment with the CAC in the aforesaid four scenarios. However, risk assessment or security impact assessment may still be needed under scenarios not covered by the Assessment Measures, by the operation of other regulations and rules. For example, under Article 55 of the PIPL a personal information protection impact assessment must be conducted before transferring personal information out of China, even if such transfer falls out of the scenarios set forth in the Assessment Measures.
Section 5 of the Assessment Measures lists the following key factors for consideration in the risk self-assessment:
- the legality, justification, and necessity of the purpose,
scope and method of the cross-border transfer and of the processing
activities by the overseas recipient;
- the scale, scope, type, sensitivity of the outbound data, and
the risks to national security, public interests or others'
legitimate rights that may be caused by the cross-border data
transfer;
- the responsibilities and obligations the overseas recipient
undertakes and whether its management, technical measures, and
capabilities for the discharge of the responsibilities and
obligations can ensure the security of the outbound data;
- the risk of data being tampered with, destroyed, leaked, lost,
onward transferred or illegally obtained or used during and after
the cross-border transfer, and whether the personal information
subjects can efficiently exercise their personal information
rights;
- whether the contract executed with the overseas recipient or
similar legal document has fully stipulates the responsibilities
and obligations to protect data security;
(vi) other matters may impact the security of the cross-border transfer.
- other matters may impact the security of the cross-border transfer.
The data handler should generate a self-assessment report, which should be submitted when filing for security assessment with the CAC.
Though "necessity of the purpose, scope and method" seems a high bar to surpass, our past experiences in data security and personal information protection impact assessment suggests that data handles are able to give a strong showing of "necessity":
- Necessity of the purpose is usually demonstrated with
supporting documents on the specific reasons for the data transfer.
In practice most of these reasons can be usually divided into two
groups: (i) the transfer is necessary because the transaction
cannot be reasonably completed without the cross-border data
transfer among the parties, with the exchange of vessel location
data and ports-related data in shipping operations, and the
exchange of clinical trial data in multi-regional clinical trials
as two examples; (ii) personal information subjects request to
transfer their data overseas, such as the case of online travel
service providers booking flights and hotels abroad for Chinese
customers.
- Necessity of the scope is demonstrated by the satisfaction of the minimalization requirement: the type and contents of the outbound data are limited within the minimum scope truly necessary for the specific purposes and the overseas retention periods are also the shortest as needed.
Another focus is the security safeguards, and data handlers are usually expected to provide the following information:
- Information on the overseas recipient's security
capabilities, such as internationally recognized security
certifications it possesses, its experiences and track records on
data processing and protection, and the adequacy of its
organizational structure and internal control measures (e.g.,
independent audit reports);
- Robust encryption and other security protocols in place to
ensure the security of the outbound data in transit and in rest,
such as commercial encryption products recognized by China's
State Cryptography Administration;
- Risk mitigation measures taken by the parties, such as reducing
the sensitivity of the data through aggregation and
pseudonymization prior to the transfer;
- The data handler's right and capability to terminate the
transfer and request for deletion, both contractually and
technically;
- A mature and executable emergency response plan and disaster recovery plan maintained by the recipient for the potential data breaches, which can be supported by a summary of such plans and documentation of its regular drills, etc.
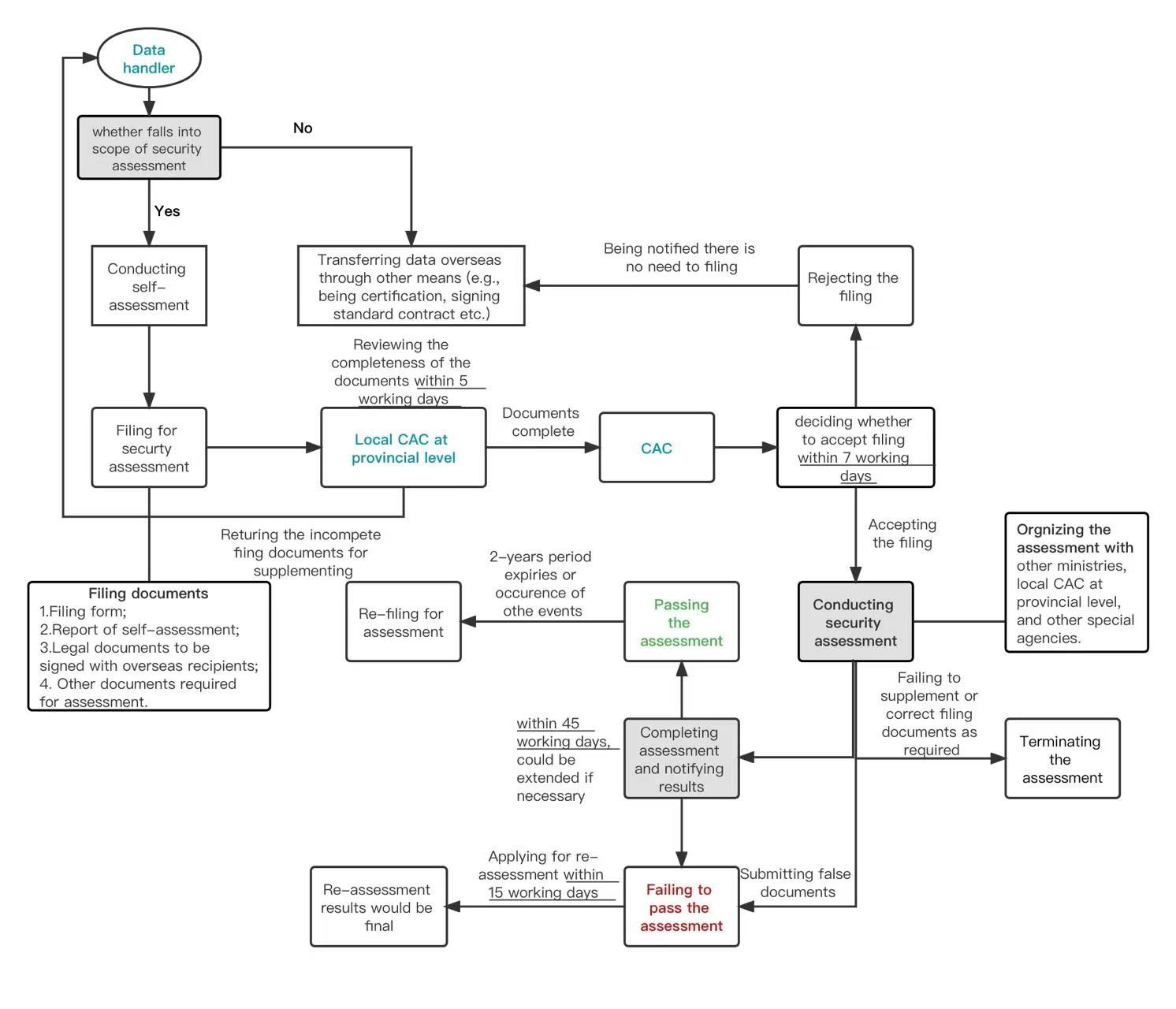
Detailed procedure for the security assessment filing
The Assessment Measures sets forth detailed procedure for the security assessment filing, and the official Q&A also provides helpful guidance on how the filing and the assessment will be conducted.
- The official Q&A suggests data handlers should submit
filing for security assessment before signing a data transfer
related contract or other legally binding document with the
overseas recipient. It further points out that, if the security
assessment filing is submitted after the legally binding document
is signed, it is recommended to condition its taking effect on the
passing of the security assessment.
- Section 7 provides the responsibilities of the cyberspace
administrations at the provincial level: they will be responsible
for checking prima facie whether the submitted documents are
complete within 5 working days upon receipt; compliant filings will
be submitted to the CAC, and non-compliant ones will be returned to
the data handlers along with an instruction on how to supplement
materials.
- Within 7 working days after receipt of the filing documents,
the CAC will decide whether to accept the filing and notify the
data handler in writing. Note, according to the official Q&A,
the CAC will reject the filing for the data transfer which are not
within the scope of security assessment, in which case the data
handler may implement the cross-border data transfer through other
means allowed by the applicable laws after receiving the rejection
notice by the CAC.
- Section 10 of the Assessment Measures further provides that the
CAC will organize the other ministries under the State Council, the
relevant local cyberspace administration at provincial level, and
other special agencies to conduct the security assessment after it
decides to accept the filing.
- Under Section 12, the security assessment will be completed
within 45 working days after the CAC sends the accepting letter to
the data handler, but such period can be extended if the
authorities deem the circumstances complex or supplemental
materials are needed.
- According to the official Q&A, there will be two results of
the security assessments organized by the CAC: (i) if passing the
security assessment, the data handler can implement the
cross-border data transfer strictly in accordance with what it has
disclosed in the filing documents; (ii) if failing the security
assessment, the data handler will be prevented from implement the
planned cross-border transfer.
- Section 13 of the Assessment Measures allows a data handler disagreeing with the result to apply with the CAC for re-assessment within 15 working days upon receipt of the result. The result of the re-assessment (if any) will be the final and binding.
Assessment of the regulatory environment of the destination by the CAC
The security assessment organized by the CAC focuses on the potential risks that the cross-border data transfer may pose to national security, public interests, and the others' legitimate rights and interests. The CAC will consider, in addition to the same factors relevant for self-assessment, "the impact on the security of the outbound data, of data security protection policies and regulations and cybersecurity environment of the country or region where the overseas recipient is located" and "whether the level of data protection of the overseas recipient meets the requirements of the laws, administrative regulations and mandatory national standards of the PRC".
The first limb eyes the overall data security regulatory environment of the destination jurisdiction, with access by authorities in the destination country as a particular concern; the second limb may lead to some disguised form of extraterritorial application of Chinese cyber laws, signaling China's ambition to shape data governance globally.
Considering the complex international political environment and geopolitical dynamics in recent years, the importance of this factor cannot be overstated. Interesting, since it is not included in the factors for self-assessment, the language suggests that the authorities review this factor sua sponte. However, given the limited resources of the authorities, it is advisable for data handlers and their overseas counterparties to take their own initiative in providing their fair assessment on this, accompanied with supporting documents.
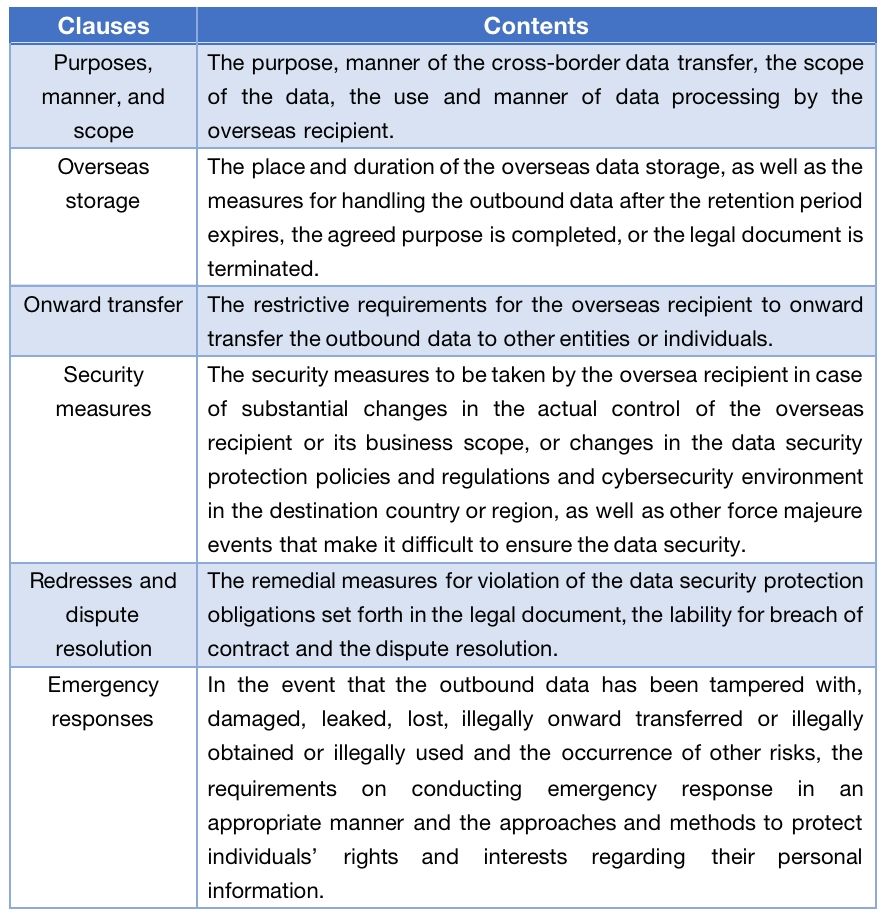
Mandatory clauses to be included in the legal document with oversea recipients
Section 9 of the Assessment Measures requires the data handler to include certain clauses in the legal document with oversea recipients, including:
Valid period for the assessment result
It should be noted that result of passing the security assessment can only remain valid for 2 years after the result is generated. If the cross-border data transfer needs to continue after the expiry of such 2-years period, the data handler should re-file for assessment at least 60 working days prior to the expiry.
In addition, Assessment Measures also require that, even still within the 2-years period, the data handler should re-file for security assessment in case of one of the following events:
- there are changes in the purpose, manner, scope and type of
providing data overseas and the use and manner of data processing
by the overseas recipient, which impact the security of the
outbound data, or overseas retention periods of personal
information and important data are extended;
- there are changes in the data security protection policies and
regulations and cybersecurity environment in the destination
country or region, or the occurrence of other force majeure events,
or the changes in the actual control of the data handler or the
overseas recipient, or the changes in the legal document between
the parties, which may impact the security of the outbound data;
or
- the occurrence of other circumstances impacting the security of the outbound data.
Under the Section 17 of Assessment Measures, the CAC may also order the data handler to terminate the transfer if it finds out the cross-border data transfer passing the assessment no longer meets the security requirements for transferring data overseas. Under such circumstances, data handler should rectify the defects and re-file for security assessment after the rectifying.
Issues to be clarified
In general, the Assessment Measures provide relatively comprehensive operational guidelines to implement the security assessment for certain cross-border data transfer as under the CSL, the DSL and the PIPL, but we noted that certain implementation issues still need to be further clarified, for example:
- The Assessment Measures provide definition of Important Data as
"the data that may endanger national security, economic
operation, social stability, public health and safety once it is
tampered with, damaged, leaked or illegally obtained or illegally
used." However, until now, the national standard on how to
identify the Important Data has not been finalized and the
catalogues of Important Data in most sectors are still under
formulation. Only after the scope of Important Data is clearly
defined, the data handlers can know whether they need to file for
security assessment for specific data transfer. Therefore,
finalizing the rules on identifying the Important Data becomes
critical for implementing the Assessment Measures.
- According to the literal meaning of Section 4(2) of current
Assessment Measures, as long as a data handler processes personal
information of more than 1 million individuals, its transfer of
personal information overseas should be subject to security
assessment organized by the CAC, regardless of the type and volume
of personal information it actually transfers. Based on this
understanding, the following is a possible case which may
arise:
A company collects and processes a large number of users' personal information (more than 1 million individuals) within mainland while such users' personal information is stored and processed in local data centers and is never transferred overseas or allowed remote access by overseas entities or individual. One day, this company plans to send three employees to a foreign country for business negotiations and it needs to provide certain personal information of these employees to the foreign partner for meeting and itinerary arrangements. Under a strict interpretation of Article 4(2) of the Assessment Measures, the company's provision of such limited personal information of three employees to a foreign partner is also subject to security assessment organized by the CAC. However, it would not be reasonable to require this company to file for security assessment for such kind of cross-border data transfer and this is not quite in line with the purposes what the security assessment mechanism is intended to achieve.
At this stage, it is unclear whether CAC will provide further clarification on this issue, or it will just reject the filing if a data handler in the above-described case files for security assessment.
- How the rectification required by Section 20 should be made also needs further clarification. For example, whether the rectification is still required if the concerned cross-border data transfer has ended and no longer continues.
Some of these issues will likely be resolved prior to the Effective Date of the Assessment Measures, while others will likely be further explained and clarified by the CAC during its enforcement of the Assessment Measures.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.

