As digital asset business becomes more pervasive in all sectors of economic activity, the cyber threat to businesses and customers alike will continue to proliferate. The Bermuda Monetary Authority (the "BMA") recognises the need for effective cybersecurity programs in all financial service sectors that it regulates, including the digital asset business sector. Digital asset businesses operating in or from within Bermuda must implement and maintain effective cybersecurity rules as per the Digital Asset Business (Cybersecurity) Rules 2018. In response to the growing implications of cybersecurity failures to customers and the reputation of the jurisdiction, the BMA has established a specific team for the supervision of licenced digital asset business's cybersecurity programs.
Every licensed undertaking must appoint a senior executive to oversee and implement its cybersecurity program and enforce its cybersecurity policies (the "CISO"). The CISO will be required to report to the Board of Directors on a regular basis and provide an annual report. In appointing the CISO, care must be exercised to ensure the proposed individual is a "fit and proper" and an individual who will fulfill the role with the appropriate level of skill pursuant to the Minimum Criteria for Licensing of the Digital asset Business Act 2018.
An application for licensing to the BMA must include relevant information on the applicant's proposed cybersecurity risk management policies and how they interact with each other including a description of how the applicant implements the 'three lines of defense' model, including the (i) risk management, (ii) internal audit and (iii) compliance functions. The BMA regard the NIST and ISO framework as the 'best practice' standards and therefore entities show refer to these standards when building their cyber compliance framework, for the Bermuda licensed entity.
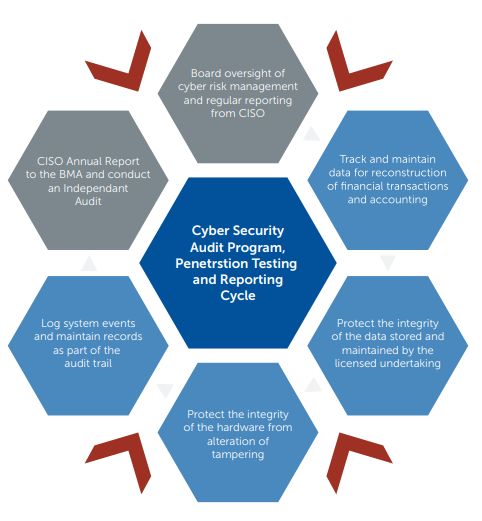
The following diagram provides an overview of the elements required in the Cyber Security Audit Program, Testing and Reporting Cycle that will be required by licensed undertakings. The four components of the audit program are shown in blue, quarterly penetration testing represented by the red arrows and the oversight and reporting required to the Board of Directors by the CISO, as well as the requirement for an independent audit, are represented in grey'.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.



