In the past two years we have witnessed significant progress in the way the corporate world operates in wholly or semi-digital environment, which was undeniably driven, among other factors, by the global COVID-19 pandemic. As a consequence of the changes of their business model, many businesses found themselves in a situation of continuous information security threats which exposed the vulnerabilities of their IT systems, assets and overall operations, as well as their human resources management.
According to European Union Agency for Cybersecurity (ENISA) Threat Landscape (ETL) report 2021, the prime threats identified in the period from April 2020 to July 2021 are ransomware, malware, cryptojacking, e-mail related threats, threats against data, threats against availability and integrity, disinformation – misinformation, non-malicious threats and supply-chain attacks1. Altogether, personal data (50%) are amongst the most disclosed data. Amongst the reported risk mitigating techniques, were discovery and classification of sensitive/personal data and application of measures for encrypting such data in transit and at rest.
On the same note, it is important to outline that in 2020 and 2021, there was a spike in non-malicious incidents, as apparently the COVID-19 pandemic multiplied human errors and system misconfigurations, leading to most of the breaches in 2020 being caused by errors, according to the abovementioned source.
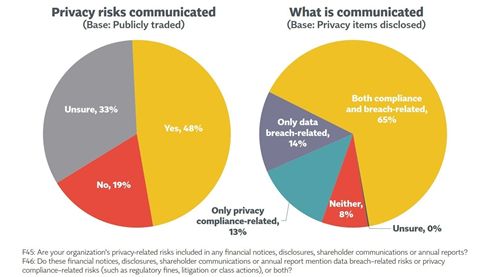
Similarly, the International Association of Privacy Professionals (IAPP)- Ernst & Young (EY) Annual Privacy Governance Report 2021 put down that half of publicly traded firms include privacy issues in disclosures and reports; most said both compliance and data breach risks are reported 2.
Fig. 13
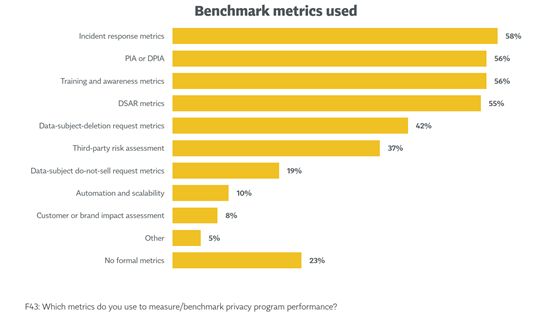
On the other hand, the most common metrics used for measure/ benchmarking privacy program performance are incident response metrics 4.
Fig. 25
As a consequence, the continuously evolving cyber-attacks, the impact of the human error-based breaches along with the lack of properly designed and implement incident respond policies, procedures and controls of many businesses often lead to significant economic losses resulting directly from the threat itself6 and/or as a liability for non-compliance with the requirements of the applicable law. The Member States Supervisory Authorities may impose a fine up to 10 000 000 EUR, or in the case of an undertaking, up to 2 % of the total worldwide annual turnover of the preceding financial year in case of a non-compliance with the requirements for notification of a personal data breach according to the General Data Protection Regulation (GDPR). On December 28, 2021, the French Supervisory Authority's (CNIL) restricted committee issued a fine of €180,000 against SLIMPAY, an authorised payment institution, for insufficiently protecting users' personal data and failing to inform them of a data breach7. Another recent example is the €80,000 fine imposed to Bank Millennium by the Polish UODO for failure to properly notify the breach and the data subjects about a personal data incident in 20218. In 2019, hackers stole personal data of around 6 million Bulgarian nationals and foreigners in an unprecedent attack against the National Revenue Agency which was due mainly to the lack of adequate technical and organizational security measures according to the investigation of the Bulgarian Supervisory Authority9. Furthermore, in the beginning of 2022 the Bulgarian Registry Agency published the home addresses of 300 000 self-employed professionals along with additional information about them not strictly related to their professional activities. Even though the national authorities are still debating if there was a technical issue which led to such disclosure or an inadequately taken decision, such action goes contrary to the principals for processing of personal data established under the GDPR.
To sweeten the pie, the exposure to reputational damages and compensation claims by affected data subjects could further increase the bill and often to overweight the administrative penalties.
In December 2021, the European Data Protection Board (EDPB) updated its Guidelines on Examples regarding Personal Data Breach10. EDPB draws the attention to the fact that the data breaches are problems in and of themselves, but at the same time they are symptoms of organizational and / or system vulnerabilities or weaknesses which could expose the businesses to regulatory, civil, or reputational risks.
The document reiterates the main obligations of data controllers and data processors in connection to data breaches and provides important guidance for the proper actions to be taken in the most common cases of security incidents. The EDPB Guidelines 01/2021 are intended to complement the previous EDPB Guidelines on Personal Data Breach Notification under Regulation 2016/679, WP 250, adopted in 2017.
The Guidelines examine in detail different scenarios of ransomware, data exfiltration attacks, internal human risk source incidents, lost or stolen devices and paper documents, mispostal and other threads, outlining the prior measures and risk assessment and mitigation and obligations of the controller or processor. The necessary actions to be taken are based on the identified risks and vulnerabilities, which are specific to a particular business and its operation, and may include the preparation of internal documentation, notification to the competent Supervisory Authority and communication to data subjects.
As next steps, it is advisable that personal data controllers and processors revise and update their internal policies, procedures and controls in the light of the new EDPB guidelines and industry best practices. This is especially important given the rather short deadline which the GDPR established for notification of a data breach to the relevant Supervisory Authority in this regard, namely 72 hours after having become aware thereof. Also, even if an organization is not obliged to appoint a DPO, it is recommended to select a particular person amongst its staff who shall be responsible to ensure the proper assessment, documentation, and, if required, notification of the competent Data Protection Authority.
Furthermore, such internal policies and procedures shall be drafted considering not only the provisions of the applicable data protection laws, but also other specific legal requirements which may apply. For instance, some Member States cybersecurity laws impose additional notification obligations on digital service providers and essential service operators which in some cases introduce even tighter deadlines than those under the GDPR.
Footnotes
1. https://www.enisa.europa.eu/topics/threat-risk-management/threats-and-trends
2. https://iapp.org/media/pdf/resource_center/IAPP_EY_Annual_Privacy_Governance_Report_2021.pdf
3. https://iapp.org/media/pdf/resource_center/IAPP_EY_Annual_Privacy_Governance_Report_2021.pdf
4. https://iapp.org/media/pdf/resource_center/IAPP_EY_Annual_Privacy_Governance_Report_2021.pdf
5. https://iapp.org/media/pdf/resource_center/IAPP_EY_Annual_Privacy_Governance_Report_2021.pdf
6. In 2020 the Portuguese energy company EDP was demanded $10.9 million by hackers as a consequence of an attack threatening to release a large amount of private client and financial information.
7. https://www.legifrance.gouv.fr/cnil/id/CNILTEXT000044609709
8. https://uodo.gov.pl/decyzje/DKN.5131.16.2021
9. https://www.cpdp.bg/index.php?p=news_view&aid=1519
10. https://edpb.europa.eu/system/files/2022-01/edpb_guidelines_012021_pdbnotification_adopted_en.pdf
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.




