Ransomware is a serious threat to businesses, and it is getting worse. While individuals were struggling to deal with ransomware attacks, fraudsters went one step further and started offering ransomware-as-a-service (RaaS). Via this business model, Cybercriminals offer a malicious kit that may be used to conduct ransomware attack services at little or no price.
Ransomware attacks surged by 25% between Q4 2019 and Q1 2020, according to a report by the Beazley Group. The average ransom payment in terms of money has also risen dramatically. Further, according to a Coveware analysis from April 2020, the average ransom payment in the first quarter of 2020 was $111,605, increasing more than 33% from the previous quarter. Ransomware attacks increased by 40% to 199.7 million incidents in the third quarter of 2020.
Ransomware attacks on international meat producers, oil pipelines, and global technological companies, as well as regional victims increased dramatically in 2021. According to Sophos research, the average ransom situation costs ten times more than the ransom paid. Importantly, only one out of every ten organizations that paid ransom received all of their data back.
The significant transition from a linear attack model to an insidious multi-dimensional Ransomware-as-a-Service (RaaS) model was noted as the driving factor behind the recent surge in ransomware attacks. As a result, businesses must address the growing threat of ransomware before it is too late.
This post explains the threat of RaaS and how to protect your system from it. It delves into the economics behind ransomware's continued popularity as a tool for cybercrime, as well as the current active ransomware variants that use ransomware as a service (RaaS), a shift in the ransomware business model that could result in a major increase in ransomware activity.
What is Ransomware as a Service (RaaS) and Why is it Such a Threat?
Ransomware is a type of malware that encrypts files and locks them up, making decryption nearly impossible without a key or exploiting encryption implementation vulnerabilities.
It's a malicious software (malware) that threatens to publish or prevent access to data or a computer system, generally by encrypting it, unless the victim pays the attacker a ransom price. The ransom demand is frequently accompanied by a deadline. The data is lost permanently if the victim does not pay on time.
Ransomware as a service (RaaS) is a subscription-based model that allows affiliates to execute ransomware attacks using pre-developed ransomware tools. Each successful ransom payment earns affiliates a commission.
By using the SaaS business model, Ransomware as a Service (RaaS) allows anyone, even those with no technical experience, to launch ransomware attacks simply by signing up for a service.
Malicious actors who lack the skills or time to generate their own ransomware variants can use RaaS kits to get started quickly and cheaply. They're easily obtainable on the dark web, where they're advertised in the same way that legal products are. Because users of RaaS do not need to be knowledgeable or even experienced to use the tool effectively, RaaS solutions enable even the most inexperienced hackers to carry out very intricate cyberattacks.
The model of ransomware-as-a-service (RaaS) is similar to that of software-as-a-service (SaaS). This subscription-based malicious model makes it simple for even the most inexperienced cybercriminal to conduct ransomware assaults. RaaS products are available on the market that eliminate the need to code malware. As a result, cybercriminals with limited technical knowledge on how to build ransomware frequently use it. Anyone can become an "affiliate" of an established RaaS product or service using this malicious model.
Ransomware is not only cheap to purchase and download; it is also simple to disseminate, with every organization becoming a target in today's digital world. The emergence of the RaaS distribution model is making it extremely easy for aspiring criminals to start a cyber-extortion business with little or no technical knowledge, resulting in a deluge of new ransomware variants.
Ransom payments are becoming more expensive, implying that ransomware is becoming more profitable for attackers. With the RaaS Model, ransomware is no longer confined to the developers who build it. Developers of ransomware are now selling their product to ransomware affiliates who use it to blackmail businesses. RaaS reduces the risk for ransomware developers by removing the need for them to carry out attacks.
RaaS lowers the cost of attacks for ransomware affiliates by allowing them to use prebuilt ransomware. RaaS broadens the ransomware threat environment by eliminating the necessity for affiliates to develop their own variant in order to carry out an attack and profit. RaaS can be equally profitable for ransomware developers as direct ransom payments because both developers and affiliates receive a share of the paid ransoms, and the malware affects more targets and occurs more frequently.
Indeed, the rise of RaaS platforms is undoubtedly one of the key causes of the massive increase in ransomware attacks. RaaS also results in a faster payout than stealing personal or credit card information. Perhaps most crucially, due to Bitcoin's anonymity, there is a lesser possibility of being caught.
Hundreds of thousands of systems have been hit by ransomware in the last 12 months, resulting in countless dollars being spent to retrieve lost files, expenditures to increase security measures, and negative reputational harm.
Several government authorities, including the FBI, advise against paying the ransom to avoid promoting the ransomware cycle. Furthermore, 50% of those who pay the ransom are likely to be targeted again by ransomware.
How Does Ransomware-as-a-Service Work?
RaaS developers build a ransomware software that has a high possibility of penetration success and a low chance of being discovered.
Phishing attacks are used to infiltrate most ransomware victims. Phishing is a technique for obtaining sensitive information, such as passwords and credit card numbers, from an apparently trustworthy source.
The most common type of phishing attack is a phishing email. Victims get a seemingly valid email, but by clicking on a link, they unwittingly activate a cyber threat.
Affiliates of RaaS send phishing emails to their victims which are quite convincing. Victims are routed to an exploit site, where the ransomware is secretly downloaded, when they click on a link.
Covid-19 phishing emails have been filling inboxes since the outbreak began. These emails appear to be highly convincing, especially to a terrified victim with shaky concerns.
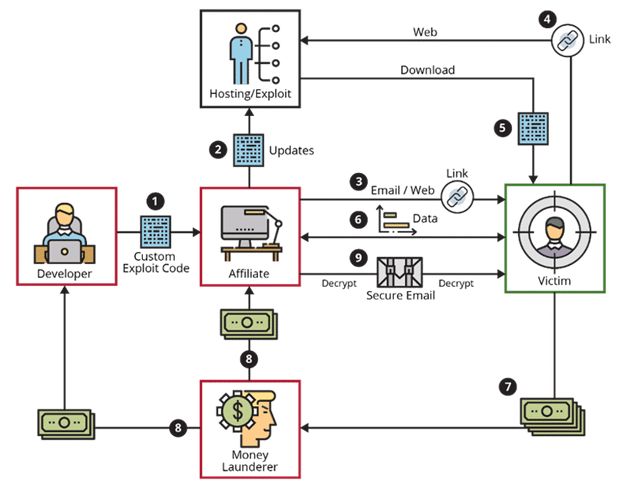
This is how the RaaS process works:
- A ransomware developer writes unique exploit code, which is then licensed to a ransomware affiliate in exchange for a fee or a share of the attack's proceeds.
- The affiliate inserts the custom exploit code to the hosting site.
- The affiliate identifies and targets an infection vector, then distributes the attack code to the victim (e.g., via malicious email or link).
- The victim goes to the website or clicks on the link.
- The ransomware is downloaded to the victim's Computer and executed.
- The ransomware encrypts the victim's files, locates more targets on the network, adjusts system parameters to ensure persistence, disrupts or destroys data backups, and hides its tracks.
- The victim is issued a ransom note and told to pay the ransom in untraceable funds, usually cryptocurrency.
- The money will be moved via various transformations by a money launderer in order to conceal the identities of the ransomware affiliate and developer.
- Once a ransom payment is paid, the ransomware affiliate may send a decryptor to the victim. The affiliate may put additional demands on the victim, or they could do nothing and leave the victim with encrypted files.
The Most Infamous Ransomware Threats
These are some of the most well-known ransomware-as-a-service:
- Satan
- Netwalker
- Cerber
- Egregor
- Hostman
- WannaCry
- Philadelphia
- MacRansom
- Atom
- FLUX
- Tox
- REvil
- Ryuk
- Encryptor
- Fakben
- ORX Locker
- Alpha Locker
- Hidden Tear
- Janus
- Ransom3
Ransomware-as-a-Service (RaaS) is on the Rise
Ransomware is becoming a huge concern around the world, with 54 percent of organizations surveyed being struck in 2017 and another 31% expected to be hit in the future. Ransomware attacks have risen in popularity in recent years.
In fact, according to SonicWall (a provider of network security and data protection products and services), the number of ransomware attacks increased by 167 times in a single year, from 3.8 million in 2015 to 638 million in 2016.
According to some statistics, nearly half of organizations were hit by a cyber-ransomware attack in 2016. Meanwhile, average ransomware demand has more than tripled, from $294 in 2015 to $1,077 in 2016. Simultaneously, the number of new ransomware families increased by 752 %, costing businesses $1 billion worldwide.
According to a January 2020 Coveware analysis, the average ransom payment jumped by 104 % from Q3 2019 to Q4 2019, rising from $41,198 to $84,116. Furthermore, according to a Coveware report from April 2020, the average ransom payment in Q1 2020 was $111,605, up more than 33% from Q4 2019.
Ransomware attacks rose by 40% to 199.7 million incidents in Q3 2020. Attacks in the United States have climbed by 139 % year over year, with 145.2 million cases reported in Q3 2020.
The abrupt transition from a linear attack strategy to an insidious multi-dimensional Ransomware as a Service model was the catalyst for the recent surge in ransomware attacks.
There are a variety of reasons why ransomware has become so ubiquitous. The first is that the businesses are unconcerned about the threats. There are various cautions about potential threats, as well as a substantial amount of advice on how to defend yourself from them. Users and businesses, on the other hand, do not protect their systems and servers as they should, and as a result, they become infected.
The second reason is more complicated: security researchers must devote a significant amount of effort to solving the problem and decrypting the data that has been affected. And it's far easier for many businesses to pay the ransom and get back to business than it is to wait.
How to Defend Yourself Against Ransomware
The most effective ransomware attack mitigation method combines staff education, defensive implementation, and constant vulnerability monitoring in your ecosystem.
- EDUCATE STAFF AND END-USER
Staff should be educated on how to recognize phishing attacks. Also Provide extensive social engineering training to your staff and end customers.
- USE A SECURITY SUITE THAT YOU CAN RELY ON.
You should install a reliable anti-malware software on your PC to defend it from this malicious threat. These intelligent tools employ powerful algorithms to detect and, in some situations, eliminate ransomware threats. Furthermore, they operate automatically in the background to protect against malware attacks 24/7.
- MAKE A BACKUP COPY OF YOUR DATA.
Any ransomware attack is designed to target users' sensitive and important data. As a result, it is critical to retain a backup of your critical data on hand in case it is required. For added security, you can back up your data on external disks or cloud servers. If you follow this simple step, you will be able to recover your data in the event of an attack.
- KEEP THE SOFTWARE ON THE SYSTEM UP TO DATE.
In general, cybercriminals hunt for known flaws in the software that runs your system. Keeping system software up to date will thus provide you with improved security against all existing and emerging cyber threats. Bug fixes, security patches, and other beneficial features are included with each software update. In addition to installing system software updates, you should maintain all apps on your device up to date for improved security.
- AVOID UNSURE LINKS AND ATTACHMENTS.
As previously stated, cybercriminals prefer to attack people through phishing emails and exploit kits. As a result, avoiding suspicious and unknown links and attachments will save you from danger. You can use your antimalware program to scan the attachment before opening it if necessary.
How Can a Cyber Security Lawyer Help in Response to a Ransomware Attack?
Ransomware is largely regarded as a legal and reputational issue, with substantial legal repercussions for institutions who do not seek legal advice early.
All data exfiltration victims are encouraged to take the necessary, but difficult, steps. Obtaining the advice of qualified security lawyers, conducting an investigation into what data was obtained, and issuing the necessary notifications as a result of the investigation and counsel are all among them.
Paying a threat actor does not relieve the victim of any of the aforementioned obligations, and given the recent outcomes, paying a threat actor not to disclose stolen data is almost useless. Other factors to consider include brand damage and long-term liability, and all of these factors should be considered before a strategy is decided.
We have skilled and experienced cyber lawyers at Olisa Agbakoba Legal (OAL) who can provide legal support and advice in cases involving cybercrime and cyber security. Our Cyber lawyers handle cybercrime cases that involve individuals, organizations, or the government, as well as cases involving e-commerce, e-contracts and digital signatures, intellectual property rights, cybersecurity, and other topics. They collaborate with stakeholders to protect against today's threats and to develop more secure and resilient infrastructure for the future.
Our Cyber Security Lawyers among other things, negotiate complex technology agreements, provide daily operational support to the agency's hunt, incident response, and vulnerability management divisions, advocate for the agency's positions in litigation, draft and negotiate legislation, and respond to audits and investigations.
Please do not hesitate to contact OAL's Cyber Lawyers if you have any questions about internet technologies or cyber crimes in Nigeria.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.

