In an era dominated by digital connectivity, safeguarding the integrity of networks and information systems has become a global imperative. China, recognizing the critical importance of cybersecurity, has introduced the draft Management Measures for Cybersecurity Incident Reporting (the Measures). The Measures outline a comprehensive approach to reporting cybersecurity incidents, aiming to minimize losses, incentivize legal compliance, protect national cybersecurity, and align with existing legal frameworks. Samuel Yang, Chris Fung, and Bill Zhou, from AnJie Broad Law Firm, explore key provisions in the Measures, shedding light on the intricacies of China's evolving cybersecurity landscape.
Purpose
Article 1 of the Measures describes the rationale behind the Measures. It emphasizes the Measures' alignment with foundational privacy, data, and cybersecurity laws in China, such as the Cybersecurity Law, the Data Security Law, the Personal Information Protection Law (PIPL), and the Regulations on the Protection of the Security of Critical Information Infrastructure.
Scope
Article 2 of the Measures sets out the Measures' scope of application to entities involved in constructing, operating, or providing services through networks within the PRC (Operators).
Regulators
Article 3 of the Measures provides, the central cyberspace administration coordinates and supervises national cybersecurity incident reporting. In contrast, local cyberspace administrations coordinate and supervise cybersecurity incident reporting within their administrative regions.
Timely reporting and incident classification
Article 4 of the Measures contains requirements for the expeditious activation of emergency response plans by Operators and mandates reporting significant, serious, and particularly serious incidents within an hour.
Annexe 1 to the Measures provides meticulously granular guidelines for incident classification. Focusing on severity and impact, Annex 1 categorizes incidents into the strata of particularly serious, serious, significant, or general, as described below, in descending order of severity.
Particularly serious cybersecurity incidents can be identified by important networks and systems facing widespread failure, precipitating a consequential shutdown and loss of functionality, national security facing a particularly serious threat, and the occurrence of other particularly serious threats such as:
- disruption to key Government websites or major news platforms exceeding a day;
- critical infrastructure interruptions persist for over six hours or significant function disruption for over 24 hours;
- impact felt by over 30% of a province's populace;
- impact on transport and utilities affecting over 10 million individuals;
- leakage of important data posing a particularly serious threat to national security;
- disclosure of personal information affecting over 100 million individuals;
- impact on information systems resulting in the widespread dissemination of harmful information;
- direct economic losses exceeding CNY 100 million (approx. $13.9 million); and
- other particularly serious threats.
Serious cybersecurity incidents can be identified by important networks and systems facing partial failure, impacting operational functionality, national security facing a serious threat, and the occurrence of other serious threats, such as:
- disruption to key Government websites or major news platforms exceeding six hours;
- critical infrastructure interruptions persist for over two hours or significant function disruption for over six hours;
- impact felt by over 30% of a city's populace;
- impact on transport and utilities affecting over one million individuals;
- leakage of important data posing a serious threat to national security;
- disclosure of personal information affecting over 10 million individuals;
- impact on information systems resulting in the dissemination of harmful information;
- direct economic losses exceeding CNY 20 million (approx. $2.8 million); and
- other particularly serious threats.
Significant cybersecurity incidents can be identified by important networks and systems facing significant system losses, impacting operational capabilities, national security facing a significant threat, and the occurrence of other significant threats, such as:
- disruption to key Government websites or major news platforms exceeding two hours;
- critical infrastructure interruptions persist for over 30 minutes or significant function disruption for over two hours;
- impact felt by over 10% of a city's populace;
- impact on transport and utilities affecting over 100,000 individuals;
- leakage of important data posing a significant threat to national security;
- Ddsclosure of personal information affecting over one million individuals;
- impact on information systems resulting in some dissemination of harmful information;
- direct economic losses exceeding CNY 5 million (approx. $695,500); and
- Other particularly serious threats.
General cybersecurity incidents can be understood as not meeting the criteria of any of the above categories. This is, in essence, a residual category.
The grade of severity experienced during a cybersecurity incident may also serve as a benchmark that allows Operators to comprehend the regulatory significance of cybersecurity incidents.
Detailed reporting requirements
Article 5 of the Measures outlines what Operators must include in their reports, ranging from incident details, impact, and harm to preliminary analyses of causes and proposed countermeasures. Specifics related to ransomware attacks, such as ransom amounts and payment details, are also mandated.
A translation of the form is provided below for reference:
Cybersecurity Incident Information Report Form
Report Time: [year/month/day/hour/minute]
Report Number: [report number]
Issued by: [signatory]
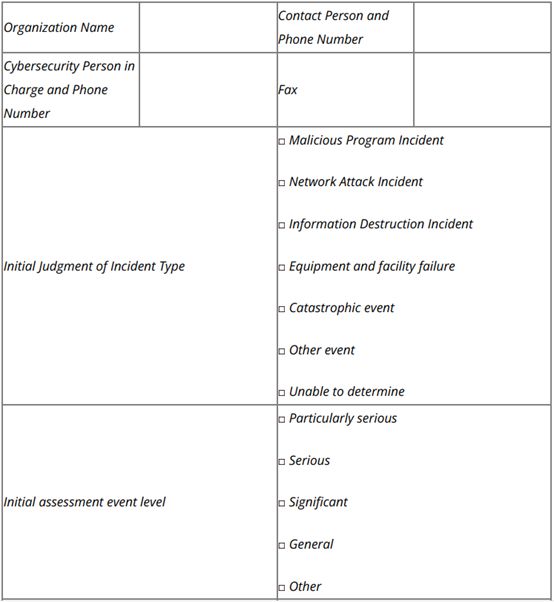
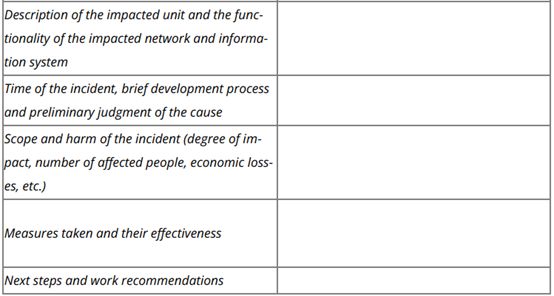

Organizations with operations in China may wish to include the above fields in any internal forms they use for incident reporting to facilitate reporting to regulators afterward.
Rigid reporting timeframes
Article 6 of the Measures acknowledges that certain incidents may require more time for a comprehensive assessment, including particularly serious or significant incidents. In such circumstances, Operators must provide initial reports within one hour, focusing on certain essential details, such as the basic information about the unit where the incident occurred, including the facilities, systems, and platforms involved, and the time, location, type, impact, and harm caused by the incident, the remedial measures taken and their effectiveness, and ransom amounts and payment details for ransomware incidents. After providing essential information within the mandated one-hour timeframe, Operators should submit supplementary information within 24 hours.
The Measures are silent on the timescales for reporting general cybersecurity incidents. However, Operators may wish to consider adopting the 24-hour standard because it is featured in other legal sources of general application and may apply to general cybersecurity incidents.
Post-incident analysis
Article 7 of the Measures mandates Operators to conduct a thorough analysis and summary within five working days of the incident's resolution. This comprehensive report should cover incident causes, emergency response measures, damages, liability management, rectification status, lessons learned, and other relevant matters.
Community involvement
Article 8 of the Measures encourages organizations and individuals providing services to Operators to remind them of reporting obligations. In cases of intentional concealment or refusal to report, organizations and individuals are empowered to escalate the matter to local or national authorities.
Public reporting and recognition
Article 9 of the Measures actively encourages social organizations and individuals to report significant cybersecurity incidents, fostering a collective approach to cybersecurity.
Enforcement and consequences
Article 10 of the Measures outlines the basis for penalties for Operators failing to comply with reporting requirements, ensuring accountability. Severe violations resulting in significant harm may, in principle, lead to more stringent penalties.
We note that one basis for penalties is the PIPL, which states the following:
'If the illegal activity[...] is of a grave nature, the violator will be ordered to make a correction, confiscated of any illegal gain, and fined up to [the higher of] CNY 50 million (approx. $6.95 million), or 5% of last year's annual revenue[...] and may also be ordered to suspend any related activity or to suspend business for rectification, and/or be reported to the relevant authority for the revocation of the related business permit or the business license; and any person in charge or any other individual directly liable for the violation will be fined [and banned from certain roles for a time].'
Exemptions for responsible Operators
Article 11 of the Measures provides leniency to Operators who have implemented reasonable and necessary protective measures, actively reported incidents, and mitigated the situation's impact. Such Operators may be exempted or face reduced penalties based on the circumstances. Article 11 can be viewed as an incentive for developing a robust internal compliance framework.
Defining cybersecurity incidents
Article 12 of the Measures clarifies that cybersecurity incidents include events caused by human factors, software or hardware defects, failures, and natural disasters, resulting in harm to networks, information systems, or data, with negative societal consequences.
Handling state secrets
Article 13 of the Measures acknowledges that incidents involving State secrets need to follow specific reporting procedures defined by relevant departments. For the avoidance of doubt, State secrets are not limited to information held by State organs or emanations. State secrets can, in principle, include (without limitation) other types of information, such as health and genetic information and mapping data, etc.
Conclusion
China's proactive stance in formulating a comprehensive cybersecurity incident reporting framework reflects its commitment to securing digital infrastructure. As the global community grapples with escalating cyber threats, understanding and adapting such measures becomes imperative for fostering a secure and resilient digital environment.
The ongoing public feedback and potential refinements to the Measures will hopefully contribute to their effectiveness in addressing the dynamic challenges of the digital age.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.
We operate a free-to-view policy, asking only that you register in order to read all of our content. Please login or register to view the rest of this article.



